Dennis E. Hamilton

|
orcmid.github.io |
orcmid.github.io>

SECURITY
>
1.5.7 2024-11-09T18:49Z |
About the Orcmid on GitHub Security-Policy Sandbox
Individual projects of Orcmid on GitHub
have separate and specific Security Policy statements, vulnerability reports,
and procedures for reporting vulnerabilities. Consult those repository
Security tabs and/or SECURITY.md files for their specific policies. The same
applies for the project repositories of others.
Review GitHub Guidance for details of GitHub support for secure reporting and handling of vulnerabilities.
The material below applies to the orcmid.github.io project repository and the web pages produced from that repository. It sets the pattern of all Orcmid on GitHub project repository security policies.
Welcome to the Sandbox
The Security Policy Sandbox is provided for completeness, as a safeguard, and as an example. Use the sandbox as a walk-through for familiarization and practice with security advisories and the vulnerability reporting process.
The web page https://orcmid.github.io/SECURITY.html provides the same Security Policy statement that can be viewed via the orcmid.github.io security tab.
Supported Versions (Sandbox case)
2024-11-06 Status: There are no code releases at the orcmid.github.io repository/project. Content consists of HTML, Markdown, images, and text files published as static GitHub Pages to the Orcmid on GitHub web site. See the project README for further details.
| Version | Supported |
|---|---|
| none | :x: |
Finding Vulnerability Announcements
Public vulnerability announcements confirm vulnerabilities, reporting their nature, their mitigation, and any actions required by those who may be employing vulnerable software versions. Occassionally, a vulnerability announcement can explain why a particular situation does not qualify as a vulnerability.
Find already-issued public vulnerability announcements, if any, for the
orcmid.github.io project/repository at
orcmid.github.io advisories.
Identify vulnerability announcements for sandbox experiments as PRACTICE announcements. Sandbox Practice reports and announcements are not published. They are only visible to their reporter and the managers of the repository.
In the unlikely case that an actual vulnerability arises at the
orcmid.github.io repository, its public announcement will be listed.
Reporting a Vulnerability
IMPORTANT: Please report vulnerability discoveries at the specific GitHub repository for software having the suspected/detected cybersecurity defect. That is where analysis, resolution, and any vulnerability announcement must occur. Use the Sandbox only as a walk-through and for practice and trial submissions to observe how the process works.
There is no support for vulnerabilities of independently-released distributions of modified forks, clones, or other derivatives of Orcmid on GitHub projects/repositories provided by others. It can be worthwhile to confirm that a derivative’s vulnerability does not arise from an original Orcmid on GitHub project; when that is the case, no support is available and any vulnerability announcement for the Orcmid project will reflect that conclusion.
What to Expect
Being a cybersecurity expert is not a requirement for reporting an observed vulnerability of any GitHub/orcmid project/repository.
Although the form provided for entering a vulnerability report is structured for use by cybersecurity experts as well as non-experts, initial vulnerability reports can be very simple:
- Reporters must have a GitHub account and be logged into GitHub to submit a report.
- English language is required, even if very brief.
- A title must be chosen for the report. For a practice report using the sandbox, please include the word PRACTICE in the title.
- There must be a brief description of the identified vulnerability. This can be a simple statement. This is also where any non-English communication should be requested.
- There must be an “ecosystem” choice. It is not necessary to know what that is. The “Other” ecosystem entry is always appropriate.
Other details and entries are optional. Some depend on expert knowledge and practices around cybersecurity procedures, including use of the Cybersecurity Vulnerability and Exposures (CVE) identifiers and associated reports, and use of the Common Weakness Scoring System (CVSS).
The Simplest Path
Where there is an established Security Policy, the page displayed for the repository’s Security tab will have a “Report a vulnerability” button.
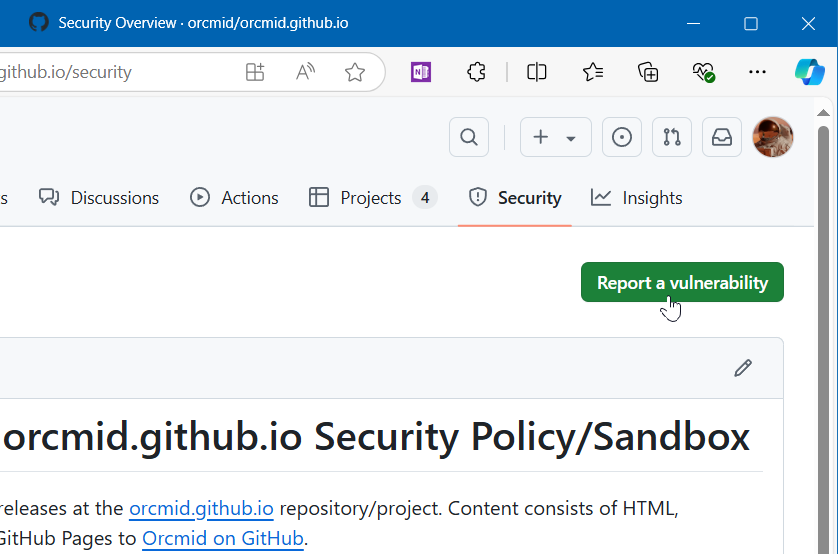
Click the button. An Advisory Details form template will open.
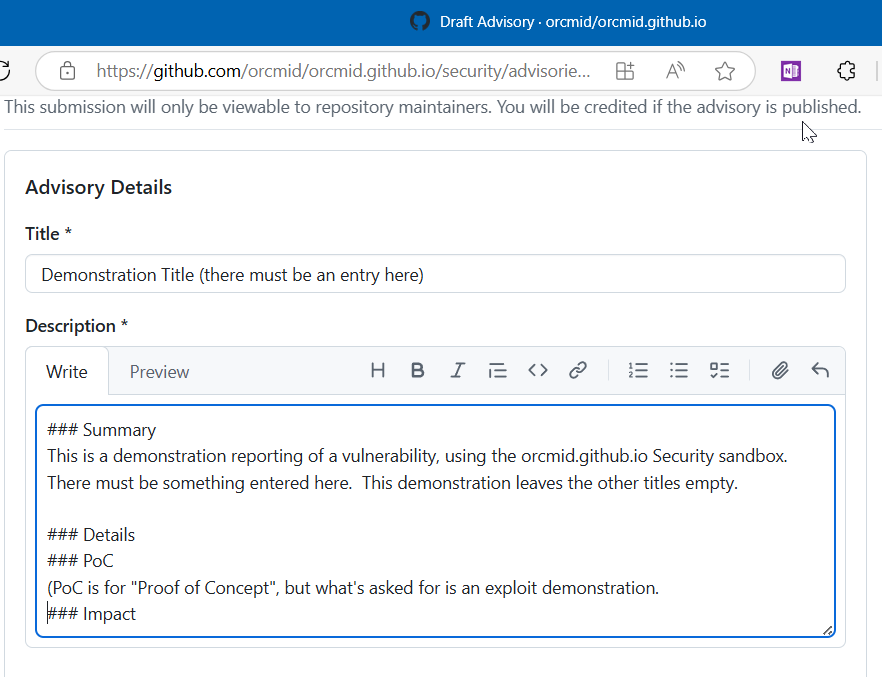
Provide a Title and enter a simple Summary.
If you have additional information, use the topics that are listed; otherwise, leave remaining topics in the template unchanged.
Scroll down in the page to the “Affected products” topic.
The “Select an ecosystem” item provides a pull-down when clicked.
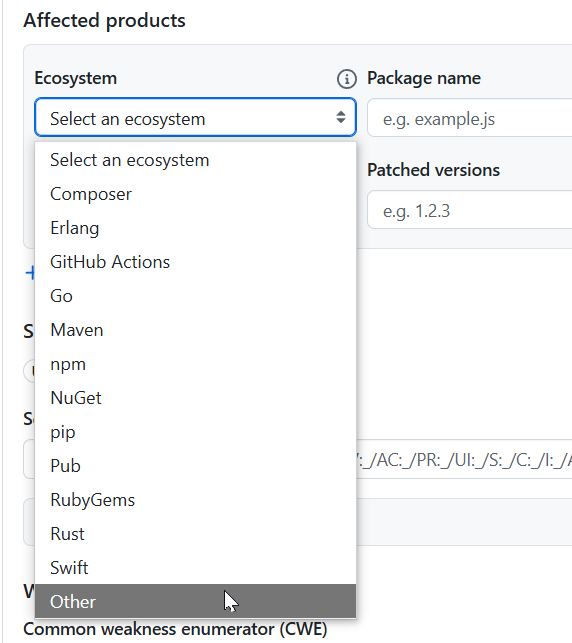
For Orcmid on GitHub projects/repositories, “Other” is always acceptable.
Scroll down to the bottom of the form and click the “Submit report” button.
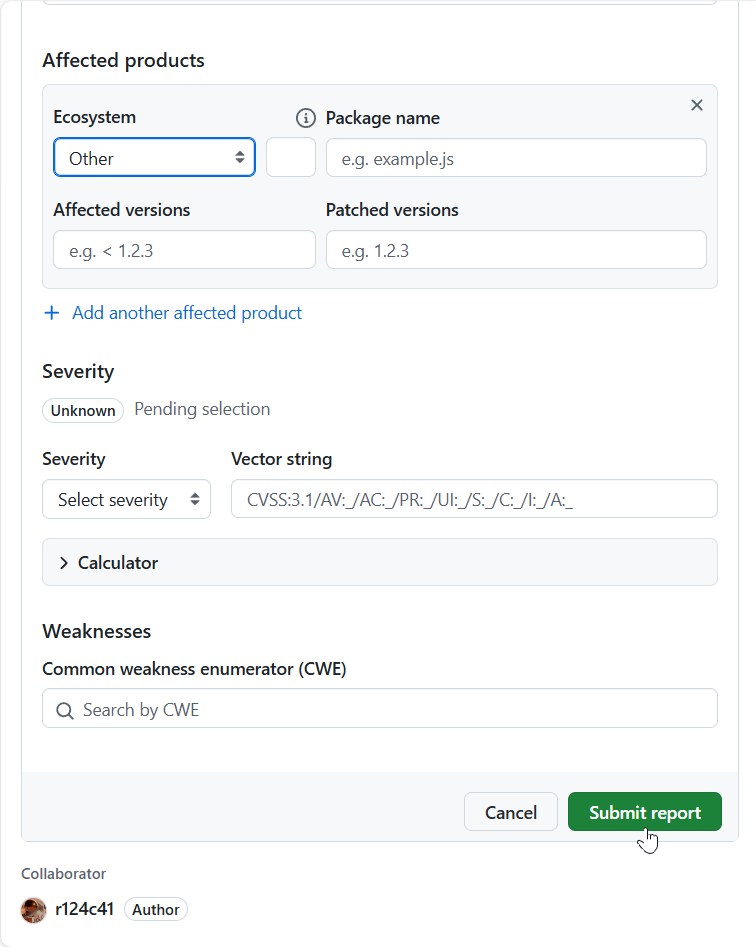
After you submit the form, there is a confirmation and invitation
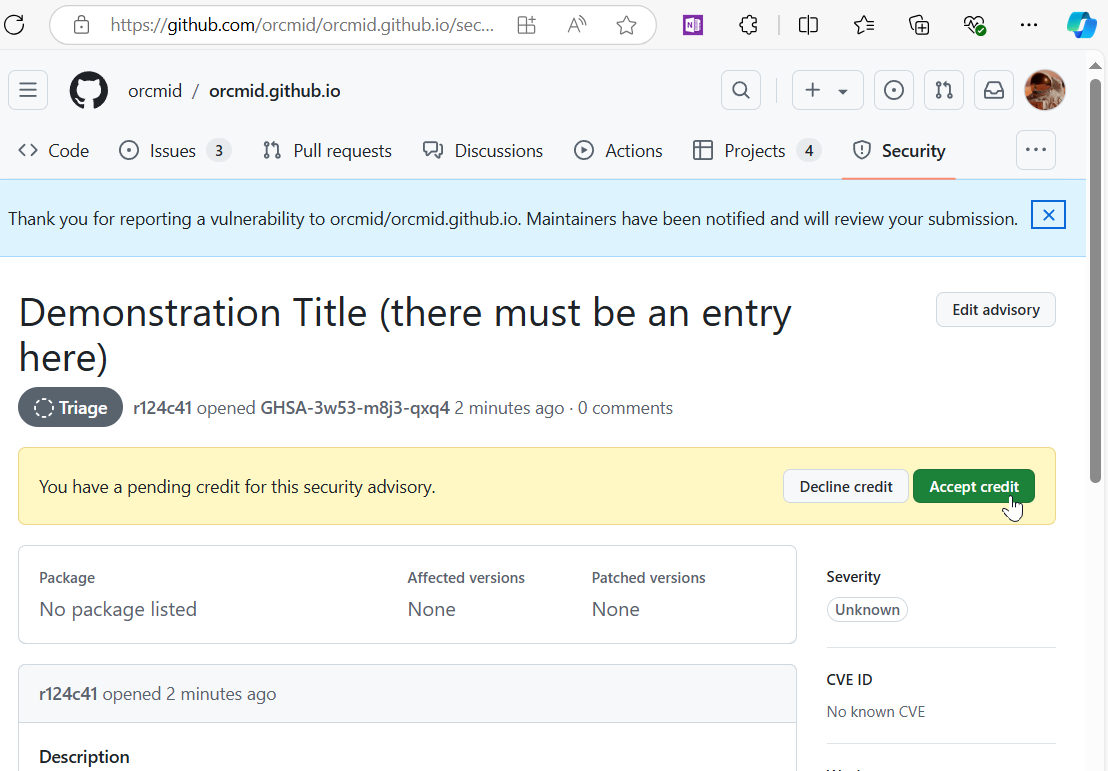
Further discussion occurs with private messages to your GitHub account.
Alternative Secure Communication
An alternative is available for those equipped to use PGP (Pretty Good Privacy) public key cryptography features.
For direct private secure communication, send an ASCII-armored PGP-encrypted report in a plaintext email to orcmid. Download and use the orcmid Apache public key.
DO NOT REVEAL anything about the vulnerability in the Subject or text of that email.
In the encrypted text, provide equivalent information to that solicited in the Description portion of the Vulnerability Report template, including the name of the Orcmid on GitHub project, the specific release (if any) and the name of files that contribute to the vulnerability.
| You are navigating orcmid.github.io material |
originally created 2024-09-04 by orcmid |
